FTC lays down the law on Errorsafe/Malvertising
December 10th, 2008
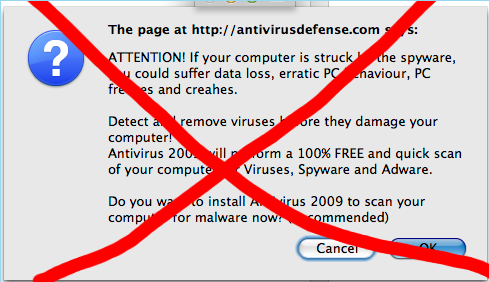
Thanks to intervention by the FTC, a US district court has issued a temporary order banning the products we have struggled with for so long in the ad-industry: WinFixer, WinAntivirus, DriveCleaner, ErrorSafe, and XP Antivirus (and more). Although primarily aimed at defending consumers, the court injection expressly bars them from performing the scam we have seen so often — “placing advertisements purportedly on behalf of a third party without that party’s consent, or otherwise attempting to conceal their own identities”.
Several networks are named directly in the suit — you probably want to make sure you aren’t working with these:
- Burn Ads
- Net Media Group
- AdTraff
- Preved Marketing
- Uniqads
According to the suit, the companies behind the scam are: Innovative Marketing (based primarily out of the Ukraine) and IMI Enterprise — and James Reno, Sam Jain, Daniel Sundin, Marc D’Souza, Kristy Ross and Maurice D’Souza named individually.
Thanks FTC!
Google Adsense showing Malvertisements
August 19th, 2008
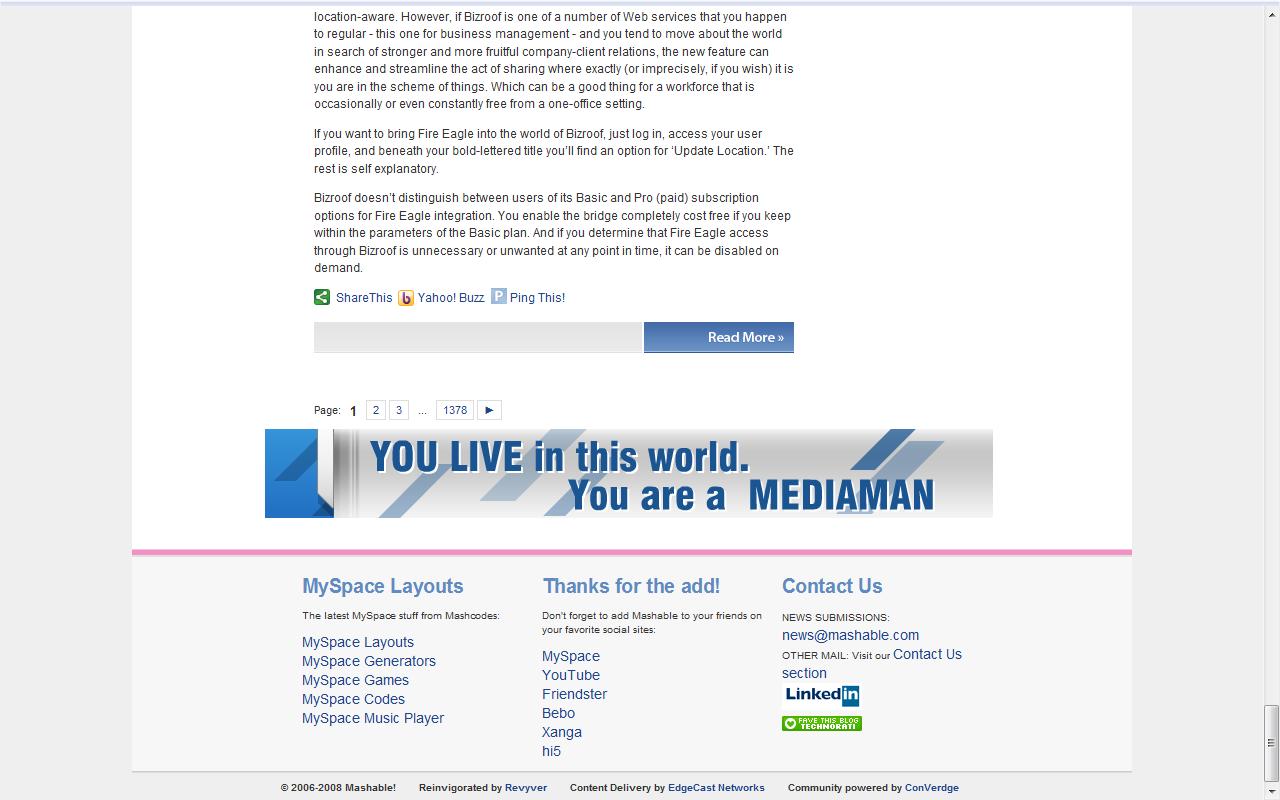
Matt Cannon sent this one over to me yesterday afternoon. He saw Google showing this lovely ad for MediaMan on mashable.com at about 1pm EST. MediaMan has been identified a long time ago as a malvertisement so it’s a surprise to see them popping up on the Adsense network. Details are below. Now I’m not posting this to shame Google (I’m sure their content team has already pulled this ad) — I’m posting this more as a call to action. It’s time that we start grouping together as an industry to help stop this. More thoughts coming on that shortly.
Screengrab of ad on Mashable:
Source of the ad (warning I would not open this if I were you):
http://pagead2.googlesyndication.com/pagead/imgad?id=CLK8lreVvKyciwEQ2AUYWjIIqyqX6hvFaHc
Screengrab of the ad:

And for the first time in a while (probably because I’m in Moscow!) I actually got the actual trigger, and got this nice popup:
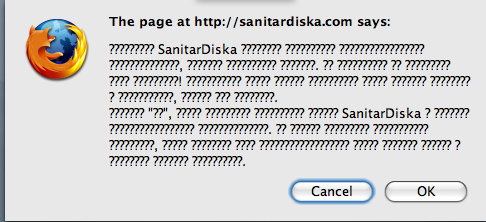
and was redirected to this lovely landing page:
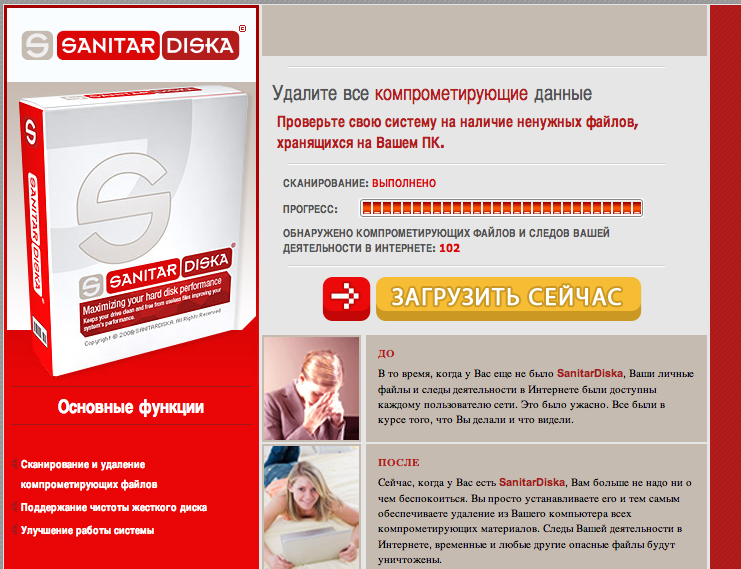
A nice list of Errorsafe sites
January 7th, 2008
I’m actually a bit embarassed here, this was sent to me about a month ago and got lost in my email with the general business of the holidays. Many thanks to Matt Cannon @ eType for doing all the research:
Spotted a variation on freecar: link. Appears to make a call to:
http://traffalo.com/statsa.php?campaign=cle9ne9t&u=1196943687109
So I then look at http://traffalo.com/ and do a WHOIS and get the IP:
http://www.networksolutions.com/whois/arin-details.jsp?domainTitle=traffalo.com&ip=190.15.73.254
I then find what is hosted on 190.15.73.254, and BINGO!
190.15.73.254 has address 190.15.73.254
Found 89 websites with the IP 190.15.73.2541) FILEPROTECTOR.COM” gping=”&POS=81&CM=WPU&CE=62&CS=AWP&SR=62&sample=0
2) MYFAVOURITESEARCH.COM” gping=”&POS=74&CM=WPU&CE=55&CS=AWP&SR=55&sample=0
3) OPENSOLS.COM” gping=”&POS=83&CM=WPU&CE=64&CS=AWP&SR=64&sample=0
4) ad2cash.net” gping=”&POS=37&CM=WPU&CE=18&CS=AWP&SR=18&sample=0
5) ad2profit.com
6) adgurman.com” gping=”&POS=51&CM=WPU&CE=32&CS=AWP&SR=32&sample=0
7) adnetserver.com
adredired.com” gping=”&POS=47&CM=WPU&CE=28&CS=AWP&SR=28&sample=0
9) adtraff.com
10) adverdaemon.com
11) adverlounge.com” gping=”&POS=40&CM=WPU&CE=21&CS=AWP&SR=21&sample=0
12) adzyclon.com
13) all-search-it.com
14) antivirussecuritypro.com” gping=”&POS=99&CM=WPU&CE=80&CS=AWP&SR=80&sample=0
15) astalaprofit.com” gping=”&POS=38&CM=WPU&CE=19&CS=AWP&SR=19&sample=0
16) b2adz.com
17) b2adz.com” gping=”&POS=63&CM=WPU&CE=44&CS=AWP&SR=44&sample=0
18) bestadmedia.com” gping=”&POS=110&CM=WPU&CE=91&CS=AWP&SR=91&sample=0
19) besteversearch.com” gping=”&POS=113&CM=WPU&CE=94&CS=AWP&SR=94&sample=0
20) bestsearchnet.com
21) brandmarketads.com” gping=”&POS=39&CM=WPU&CE=20&CS=AWP&SR=20&sample=0
22) candid-search.com
23) cashloanprofit.com” gping=”&POS=36&CM=WPU&CE=17&CS=AWP&SR=17&sample=0
24) casinoaceking.com
25) co-search.com
26) deuscleanerpay.com” gping=”&POS=77&CM=WPU&CE=58&CS=AWP&SR=58&sample=0
27) didosearch.com
28) easybestdeals.com
29) eroticabsolute.com” gping=”&POS=27&CM=WPU&CE=8&CS=AWP&SR=8&sample=0
30) favourable-search.com
31) fileprotector.com
32) findbyall.com
33) freerepair.org
34) friedads.com” gping=”&POS=42&CM=WPU&CE=23&CS=AWP&SR=23&sample=0
35) fulsearch.com” gping=”&POS=114&CM=WPU&CE=95&CS=AWP&SR=95&sample=0
36) getfreecar.com
37) great4mac.com
38) kazilkasearch.com
39) libresystm.com” gping=”&POS=116&CM=WPU&CE=97&CS=AWP&SR=97&sample=0
40) loffersearch.com
41) luckyadsols.com” gping=”&POS=67&CM=WPU&CE=48&CS=AWP&SR=48&sample=0
42) magicsearcher.com” gping=”&POS=75&CM=WPU&CE=56&CS=AWP&SR=56&sample=0
43) manage-search.com
44) megashopcity.com
45) mightyfaq.com” gping=”&POS=43&CM=WPU&CE=24&CS=AWP&SR=24&sample=0
46) misc-search.com
47) moneycometrue.com” gping=”&POS=41&CM=WPU&CE=22&CS=AWP&SR=22&sample=0
48) moneypalacecash.com” gping=”&POS=118&CM=WPU&CE=99&CS=AWP&SR=99&sample=0
49) moneypalacecash.com” gping=”&POS=21&CM=WPU&CE=2&CS=AWP&SR=2&sample=0
50) myhealth-life.org” gping=”&POS=82&CM=WPU&CE=63&CS=AWP&SR=63&sample=0
51) myonlinefinance.com” gping=”&POS=94&CM=WPU&CE=75&CS=AWP&SR=75&sample=0
52) mysurvey4u.com
53) mytravelgeek.com” gping=”&POS=101&CM=WPU&CE=82&CS=AWP&SR=82&sample=0
54) netturbopro.com
55) opensols.com
56) pcsupercharger.com
57) popadprovider.com” gping=”&POS=65&CM=WPU&CE=46&CS=AWP&SR=46&sample=0
58) popupnukerpro.com
59) prizesforyou.com” gping=”&POS=100&CM=WPU&CE=81&CS=AWP&SR=81&sample=0
60) roller-search.com
61) rombic-search.com
62) rombic-search.com” gping=”&POS=32&CM=WPU&CE=13&CS=AWP&SR=13&sample=0
63) se7ensearch.com
64) search-the-prey.com
65) searchcolours.com” gping=”&POS=78&CM=WPU&CE=59&CS=AWP&SR=59&sample=0
66) searchmandrake.com
67) searchonline-ease.com
68) searchoperation.com
69) searchvirtuoso.com
70) sellmoresoft.com” gping=”&POS=97&CM=WPU&CE=78&CS=AWP&SR=78&sample=0
71) sellmosoft.net
72) selvascreensaver.com” gping=”&POS=102&CM=WPU&CE=83&CS=AWP&SR=83&sample=0
73) sharpadverts.com” gping=”&POS=66&CM=WPU&CE=47&CS=AWP&SR=47&sample=0
74) shivanetworking.com” gping=”&POS=62&CM=WPU&CE=43&CS=AWP&SR=43&sample=0
75) simplesamplesearch.com
76) softwcs.com” gping=”&POS=108&CM=WPU&CE=89&CS=AWP&SR=89&sample=0
77) stratosearch.com
78) tallgrass-seach.com
79) traveltray.com
80) treekindsearch.com
81) wewillfind.com” gping=”&POS=109&CM=WPU&CE=90&CS=AWP&SR=90&sample=0
82) wontu-search.com” gping=”&POS=46&CM=WPU&CE=27&CS=AWP&SR=27&sample=0
83) workhomecenter.com
84) yourseeker.com
85) yourshopz.com” gping=”&POS=103&CM=WPU&CE=84&CS=AWP&SR=84&sample=0
86) yourteacheronline.com” gping=”&POS=106&CM=WPU&CE=87&CS=AWP&SR=87&sample=0
87) zappinads.com” gping=”&POS=107&CM=WPU&CE=88&CS=AWP&SR=88&sample=0
88) zooworld-search.com
89) zooworld-search.com” gping=”&POS=30&CM=WPU&CE=11&CS=AWP&SR=11&sample=0
Enough is enough — time to restrict ad permissions
September 8th, 2007
They’re getting smarter and smarter! According to SC Magazine the malicious banner ads have hit up Myspace, Photobucket, Bebo and and Ultimate Guitar. Interestingly enough:
The fictitious ads know to remove the malicious code if they detect the known IP addresses of the Right Media scanning servers.
Well, I say enough! Thanks to Mandy Singh for the tip about using flash permissions to restrict what the ad can do on the site. The malicious ads use javascript to both determine whether or not to and actually execute on the drive-by installs. This permission can be restricted by using the AllowScriptAccess flag. I’ve tested this on various errorsafe flash files and indeed it prevents them from launching an install.
So here’s my proposal — the default for serving any ad should always be with restricted script access. Of course this will probably break certain rich-media ads, which should be individually certified as ‘safe’ and given explicit approval to execute javascript.
Couple more errorsafe
August 3rd, 2007
Sorry I’ve been slacking here, couple new ones — eBooks, MediaMan and Singlesnet
WSJ Article on Online Ad Safety
July 20th, 2007
The Wall Street Journal posted an article this morning titled Hackers Can Now Deliver Viruses via Web Ads. Although not very detailed it does bring some needed attention to these issues.
HauteSecure – Good idea, bad implementation
July 11th, 2007
Via TechCrunch I found out about a new service called ‘Haute Secure’. The idea is this — install a nice browser plugin that watches for embedded content (e.g. bad ads?) and blocks them if they are found unsafe. In theory I think this is a great idea — consumers need some level of protection from the scams I’ve documented prior on this blog propagated by companies such as Errorsafe & Winfixer.
Sadly this service is seriously flawed right now. Check this out:
and
Yeah — so great in theory, but when you flag feedburner.com as unsafe and errorsafe.com as safe then there are some serious issues with the service. Some more examples:
Unsafe
- googlesyndication.com
- myspace.com
- photobucket.com
- yieldmanager.com
- cpxinteractive.com
Some Safe URLS:
- winfixer.com
- drivecleaner.com
- workhomecenter.com
- mysurvey4u.com
I firmly believe that url blacklists aren’t going to be able to provide much an answer. In certain cases such as errorsafe.com or mysurvey4u.com it makes total sense, but the challenge arises when legitimate domains are used to serve illegitimate content. For example, what if “akamai.com” was put as a banned url? Haute Secure has the right idea, but it needs some work. I hope they’re working on some more robust techniques. If I were them I would work on analyzing actionscript and javascript before allowing the browser to execute the code.
Errorsafe on CareerBuilder.com
July 4th, 2007
I’ve been quite a few emails about my ErrorSafe page, both from publisher and end-users, but not a single one from an ad-network. Interestingly I’ve gotten two separate comlaints about ErrorSafe on CareerBuilder.com. The first complaint I received was from April 22nd:
Just came across this information after receiving an odd message from drivecleaner.com. I was on Careerbuilder.com at the time, which doesn’t surprise me since my resume was “picked up” by some email scammers (phishing for SSN#s I guess) from that site recently. I have also been browsing EBay quite a bit lately. What exactly do I have to fear, as a consumer, from these heavy-traffic sites? I rarely click on the types of ads you have shown here, but now I NEVER will. I’ll just go directly to any website I want to visit. I work on an Apple MacBook,which I believe to be far less susceptible to viruses, and this drivecleaner showed up while I was browsing in Firefox. Any thoughts?
Then this morning, I received a second one:
Hello, I know very little about techie things, but i am on a mac and get the errorsafe messages on the careerbuilder website.
So, I thought I’d take a look, and sure enough what do I see?
Apologies for the crappy windows paint outlining but what you see there is a “mysurvey4u.com” ad on careerbuilder.com. If this name doesn’t ring a bell, I’ve already identified this as a fake front for running Errorsafe/Drivecleaner/Winfixer ads on my Errorsafe Page. Of course I have a tracer open, and what do we see? (Displayed URLs edited for clarity)
14:03:40.937[344ms][total 344ms] Status: 200[OK] GET http://oascentral.careerbuilder.com/RealMedia/ads/adstream_sx.ads/careerbuilder.com/JobSeeker[...]
14:03:41.640[375ms][total 375ms] Status: 200[OK] GET http://a248.e.akamai.net/[...]/oascentral-s.realmedia.com/RealMedia/[...]/Mysurveys_Burnads_120_ROS_Jul07[...]
Now I”m mostly guessing here, but it looks to me like CareerBuilder is hosting this creative themselves using 24/7 RealMedia’s Open Adstream adserver. Looking at the URL I’m going to guess that the creative for MySurvey4U was supplied by “BurnAds” — which from their website appears to be yet another online advertising/marketing/ad-network.
If you happen to have a contact at CareerBuilder they could probably use a little education on ad-safety.
Some more errorsafe
June 17th, 2007
Sorry for the hiatus… been traveling quite a bit this past week and haven’t had much time to post. Thankfully a kind publisher stirred me awake with an email about a new errorsafe creative that I hadn’t listed yet. So did some more digging and here are a bunch of new ones:
Gamefly:
Weightwatchers
Going forward I’m just going to put the name and screenshot as the rate with which these are coming I simply don’t have the time to post the actionscripts and raw flash for all of these.
Four new Errorsafe/Winfixer scams
May 30th, 2007
Apologies for the delay in updating my errorsafe page. Will try to do it more often — found a whopping 5 new scams this past month! Check out the page here. Added details for five ads with sketchy code embedded in them: Flycell.com, How2Vacation.com, nCyber iPod, Speedbit.com & eDiets.com. Some screencaps of the creatives below… check the page for actionscript and full flash files:





